Product Overview
DataSecurity Plus is a one-stop solution for data visibility and security. This document gives a brief overview of DataSecurity Plus, its capabilities, benefits, and more.
What is DataSecurity Plus?
DataSecurity Plus is a real-time file server auditing, data risk assessment, and data leak prevention solution. It audits file changes and policy violations, identifies issues relating to non-compliance, alerts admins, and responds to incidents to mitigate potential damage to data stores.
ManageEngine DataSecurity Plus makes it easy to:
-Gain visibility into file accesses, changes, and share and NTFS permissions.
-Monitor file integrity, and alert admins about anomalous activity.
-Detect sensitive data with both content and context analysis.
-Improve storage efficiency, and simplify junk file management.
-Prevent data leaks via USBs and workstations.
Specifications
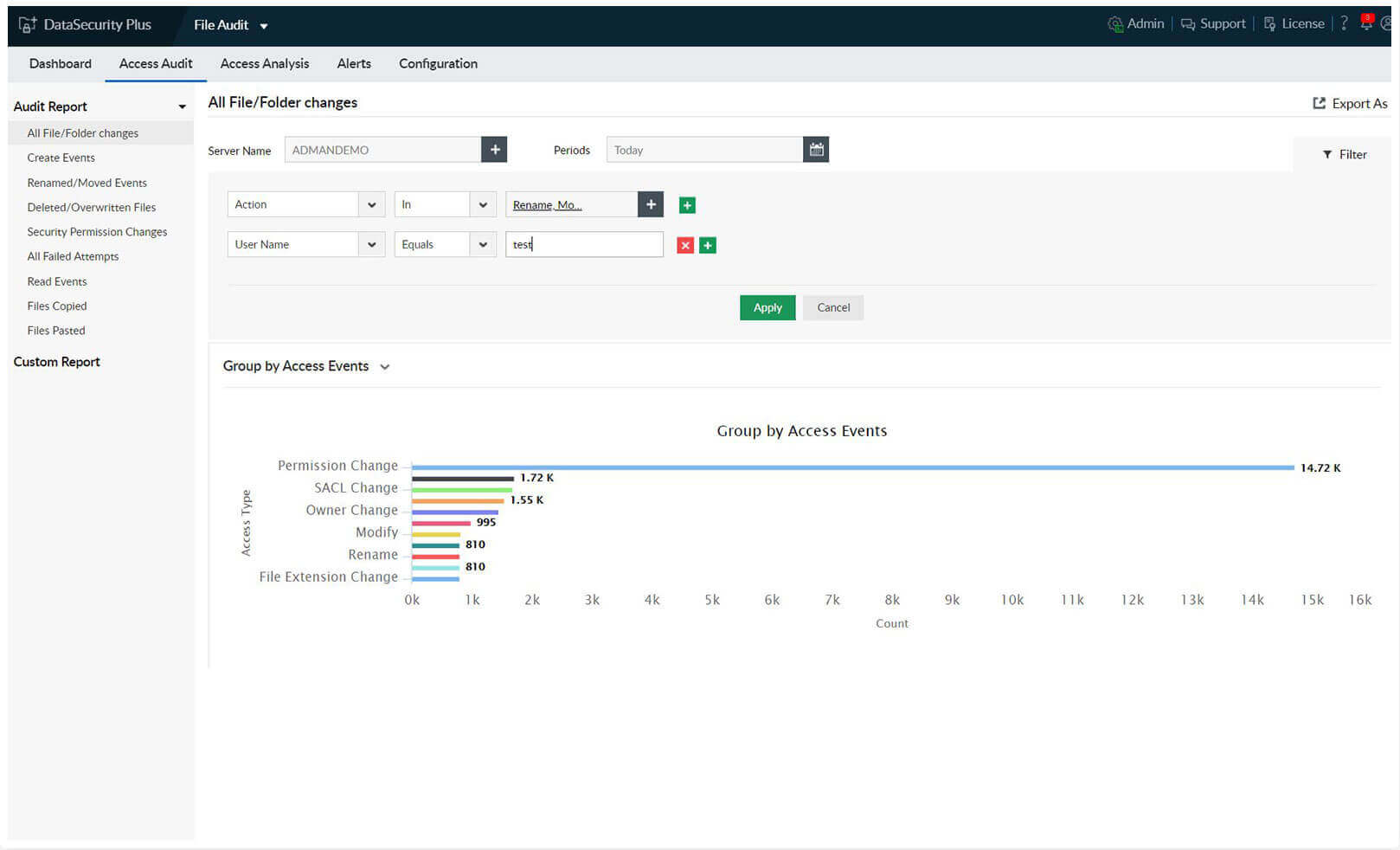
Audit file and folder accesses
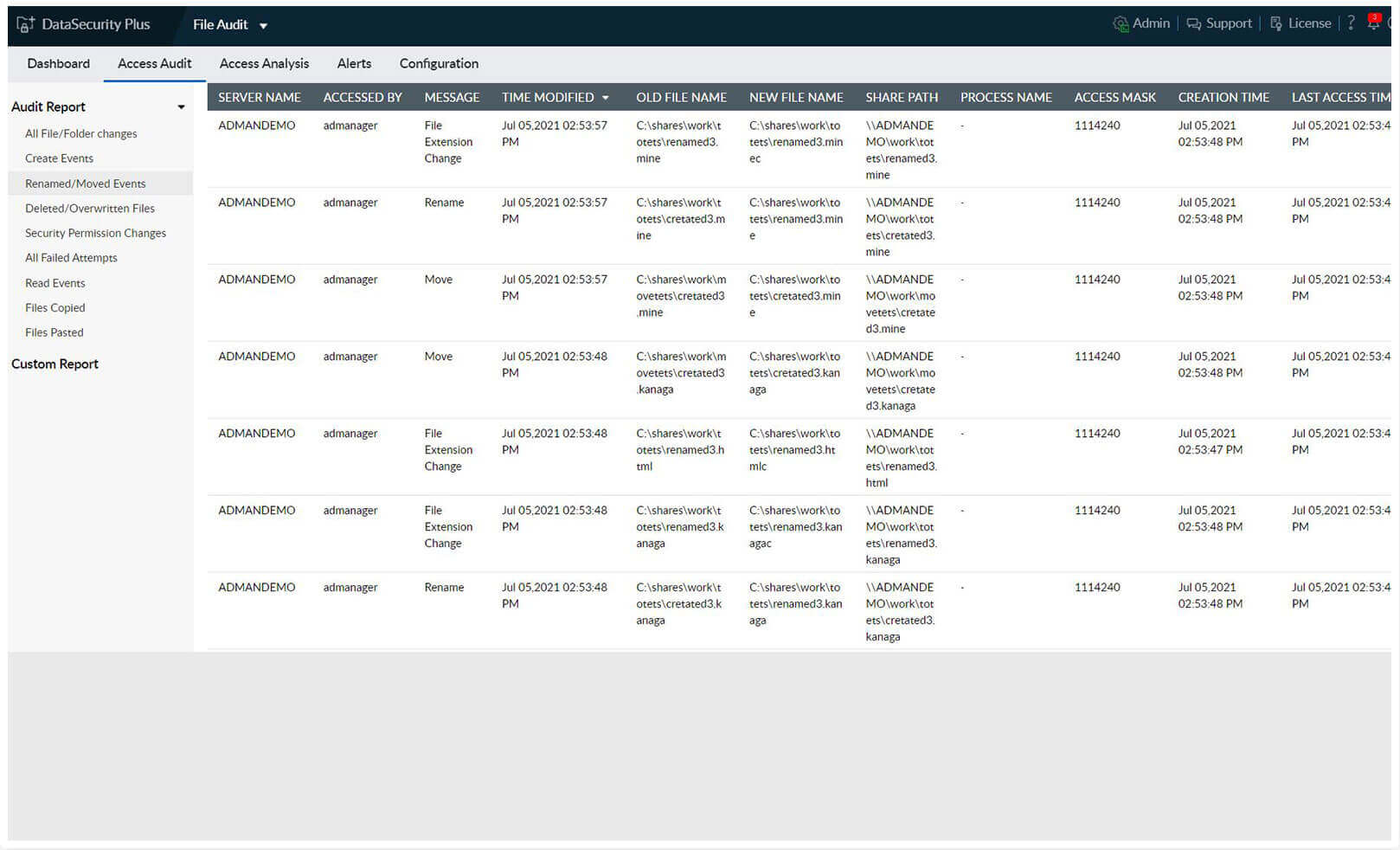
-Monitor and report on a wide range of file activities including create, delete, modify, overwrite, rename, move, read, etc. in real time.
-Track and record a complete audit trail of all files copied by auditing your clipboard for Ctr+C and right-click copy actions.
-Audit and analyze both successful and failed file access attempts made by your employees to prevent future security issues.
-Maintain a detailed record of all file activities, along with details on who accessed what, when, and where.
-Analyze audit data to identify your organization's most active user, most accessed file, process used to access most files, and more.
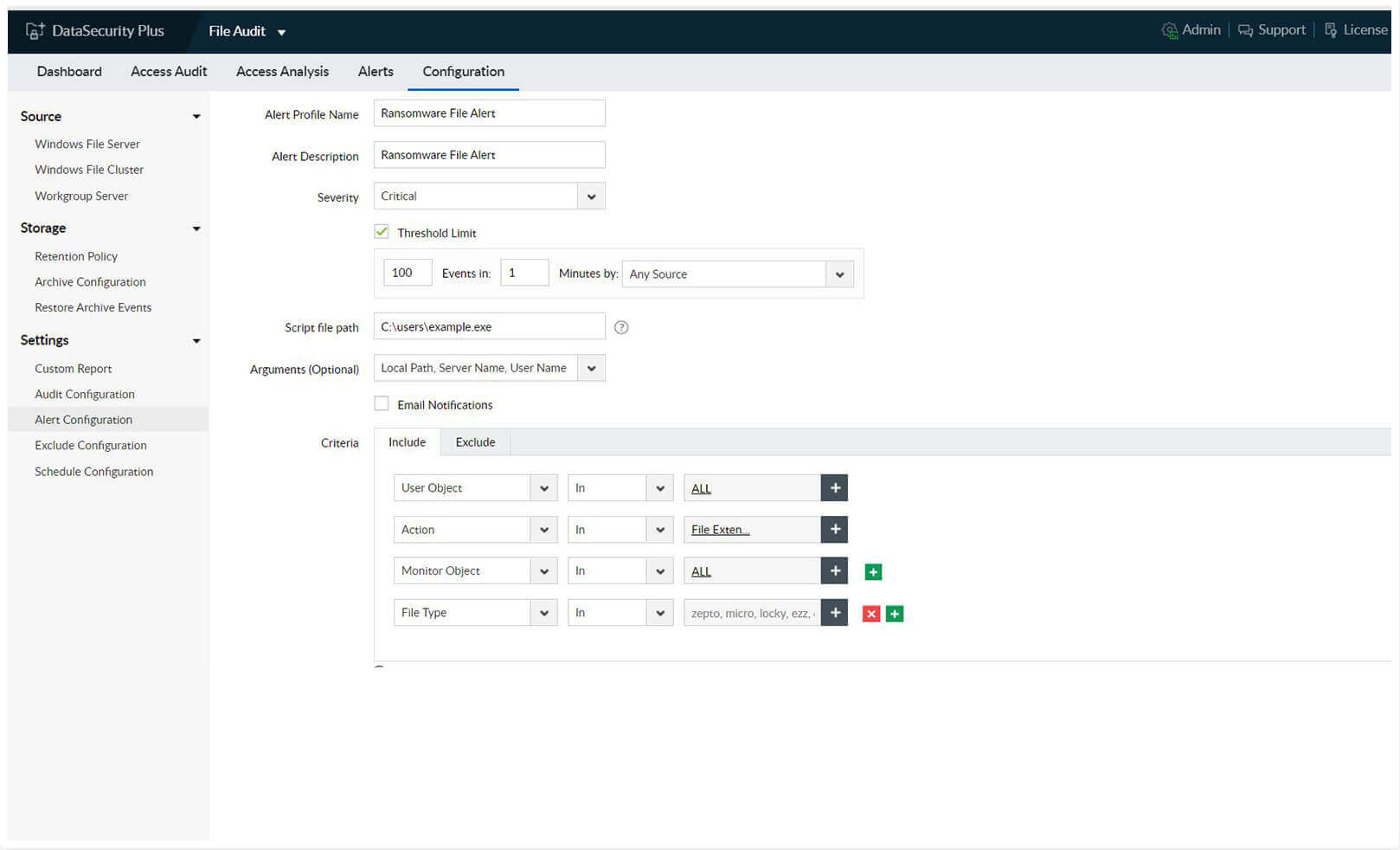
Detect and quarantine ransomware attacks
-Spot ransomware attacks quickly using telltale indicators such as sudden surges in file rename, move, and permission change activities.
-Notify admins and other stakeholders instantly via email as soon as the potential ransomware attack takes root.
-Use an automated incident response system to shut down the infected device, disable or disconnect the rogue user's session, and more.
-Use our actionable, accurate audit data to conduct a root cause analysis to identify patient zero and how the infection spread.
-Locate ransomware-corrupted files using our prebuilt, up-to-date library of known ransomware file types to protect your organization's critical data.
Monitor file integrity to detect potential threats
-Generate instant email notifications when there is a sudden spike in failed attempts to modify or delete business-critical files.
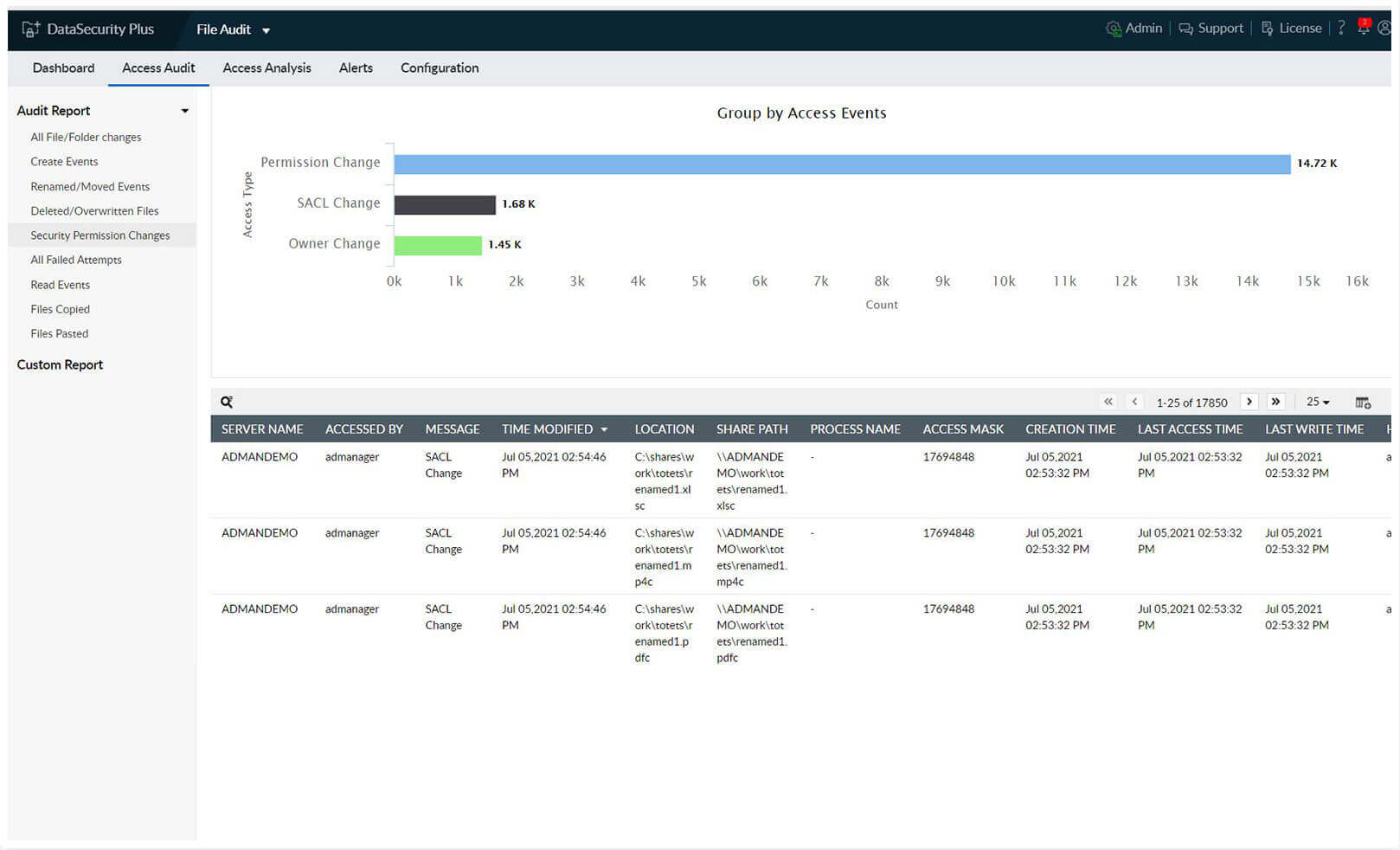
-Spot privilege abuse early on by tracking frequent permission changes, SACL changes, owner changes, and more.
-Stay aware of indicators of compromise, such as a file activity during non-business hours, and more.
-Identify the root cause of critical security events using detailed forensic data, and generate clear and concise audit records.
-Selectively monitor and scrutinize the file activities of untrustworthy users and groups for unwarranted activities.
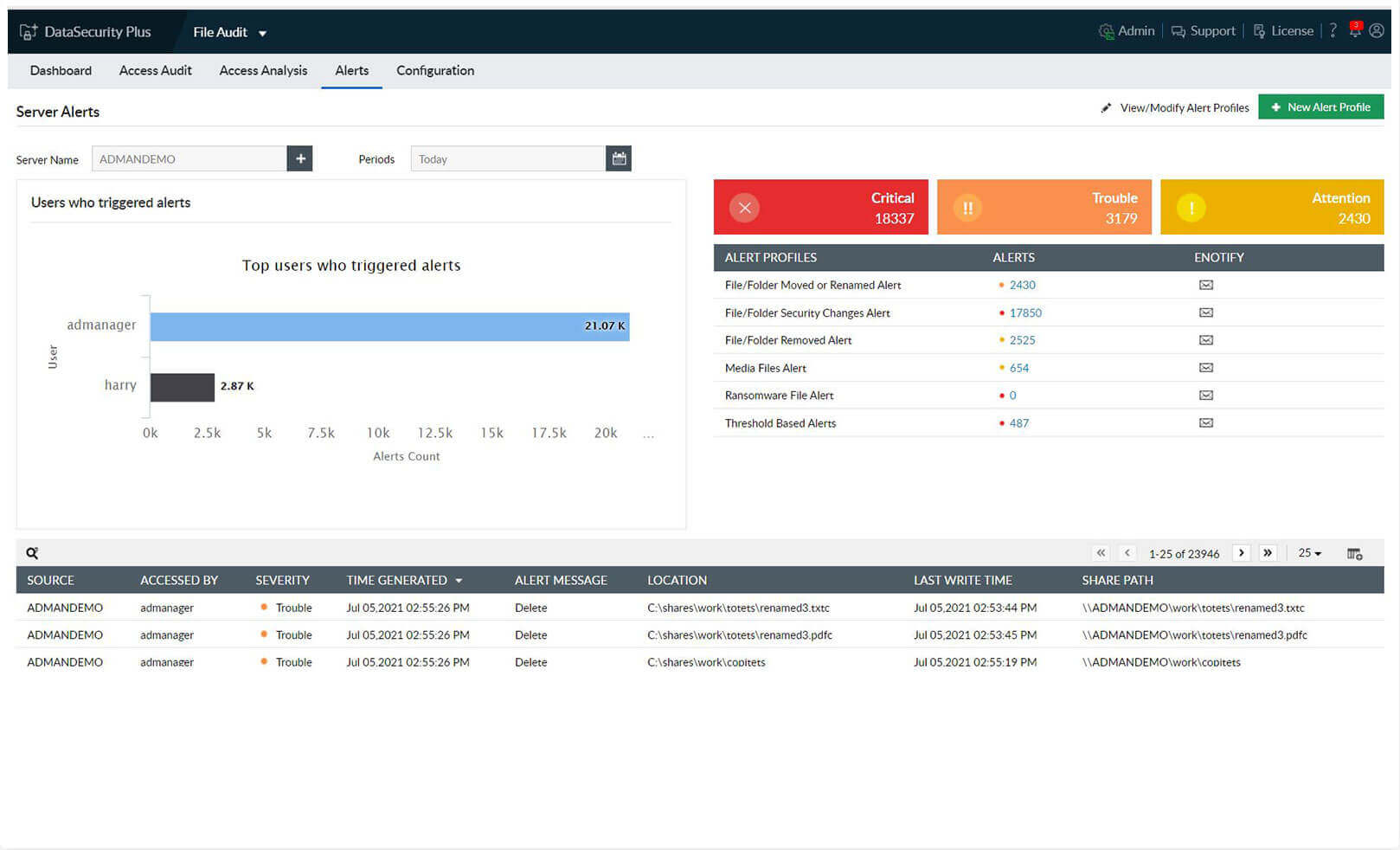
Get instant file change notifications
-Trigger instant email alerts on observing anomalous changes, like when an unusual volume of files are deleted, overwritten, or moved.
-Spot malware intrusions by looking out for a sudden spike in file modifications in a short period, and trigger instant threat response mechanisms.
-Create and manage custom alerts to spot organization-specific issues like hoarding of media or large files.
-Categorize and analyze alert data based on its severity, i.e., attention, trouble, and critical.
-Actively monitor your file servers for signs of compromise, such as multiple permission changes, file extension modifications, etc.
Comply with regulatory mandates.
-Address critical requirements of PCI DSS and HIPAA regulations using change detection.
-Identify the root cause of security incidents using accurate forensic data, and generate clear and concise audit records.
-Generate and archive audit trails to ensure accountability for all file activity.